Managing secrets (passwords, API keys, certificates) securely is critical in modern application development. HashiCorp Vault is a robust solution built to securely manage and control access to these secrets. In this post, we’ll explore how to get started with Vault, from setup and initialization to using it in a secure manner.
What is HashiCorp Vault?
HashiCorp Vault is a powerful solution for securely managing confidential data like API tokens, passwords, certificates, and other sensitive credentials. It's commonly adopted by teams operating in cloud-native or DevOps settings where strong security and access control are essential. Vault offers a centralized and secure way to handle secrets, with detailed access management and built-in protection mechanisms.
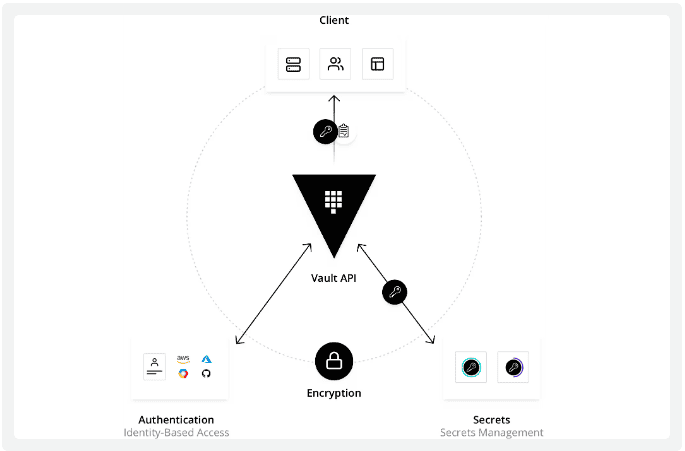
Workflow of Vault:
Vault primarily operates using tokens, each of which is linked to a client's policy. Policies in Vault are path-based, defining specific rules that restrict actions and access to designated paths for each client. Tokens can be created manually and assigned to clients, or clients can log in to obtain one dynamically. The following illustration demonstrates Vault's core workflow.
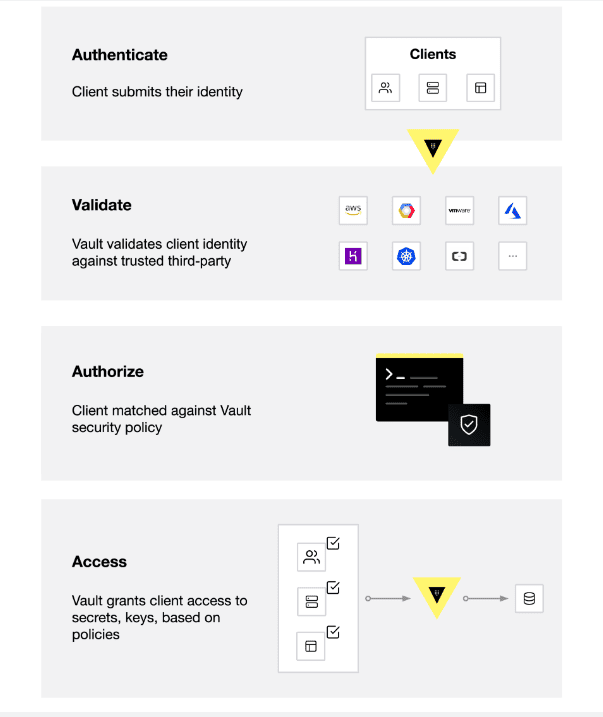
The Vault workflow consists of four key stages:
1. Authentication – A client provides credentials that Vault verifies to confirm their identity. Once authenticated through an authentication method, Vault generates a token linked to a specific policy.
2. Validation – Vault cross-checks the client’s identity with trusted external systems such as GitHub, LDAP, and AppRole to ensure authenticity.
3. Authorization – Vault applies security policies to determine what actions the client is permitted to perform. These policies specify which API endpoints and resources the client can access using their assigned token.
4. Access – Based on the assigned policies, Vault grants the client access to secrets, encryption tools, or other secured resources. The issued token allows the client to interact with Vault for future operations.
Key Uses of Vault:
* Secret Storage: Vault provides a secure location to store sensitive information, preventing unauthorized access.
* Dynamic Secrets: Vault can generate secrets dynamically, such as database credentials, which can be automatically revoked when no longer needed.
* Encryption as a Service: Vault allows encryption and decryption of data without exposing encryption keys, offering a high level of data security.
* Identity-based Access: Vault supports various authentication methods like tokens, LDAP, and AppRole, allowing role-based access control (RBAC) to secrets.
* Audit and Monitoring: Vault tracks all access to secrets, generating logs for auditing and compliance purposes.
Benefits of Using Vault:
* Centralized Secret Management: Vault centralizes the management of secrets, ensuring consistency and reducing the risks of managing secrets in an ad-hoc way.
* Enhanced Security: Vault offers encryption, role-based access controls, and the ability to rotate secrets periodically, all of which improve the overall security posture.
* Compliance and Auditing: Vault’s built-in logging and audit features make it easier to meet compliance requirements and track access to sensitive data.
Features
* Secure Secret Storage: Enables Odoo to store credentials, API keys, and other sensitive data securely in HashiCorp Vault.
* Secret Retrieval: Provides an API-based approach to fetch secrets dynamically from Vault whenever required.
* Role-Based Access Control: Guarantees that only permitted users or components have access to designated secrets.
* Automated Secret Rotation: Supports periodic secret updates to enhance security and minimize risk exposure.
* Audit Logging: Tracks all secret access requests to maintain a comprehensive security audit trail.
* Multi-Backend Support: Compatible with multiple Vault backends such as AWS, GCP, and Azure.
Install Hashicorp Vault for Ubuntu
Now, let's take a look at how to set up Vault on Ubuntu. Here are step-by-step instructions on how to install, configure, and use HashiCorp Vault on an Ubuntu system.
Prerequisites
Before you begin, make sure you have the following:
* Ubuntu 20.04 or later.
* Sudo privileges or root access.
Step 1: Install HashiCorp Vault
The first step in installing Vault is to download and add the HashiCorp GPG key. This key will be used to verify the authenticity of the Vault packages you will install.
Command:
wget -O - https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
Step 2: Add HashiCorp’s APT Repository
Next, you need to add HashiCorp's APT repository to your system’s list of sources. This tells the system where to look for Vault packages.
Command:
echo "deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
Step 3: Update APT and Install Vault
Now that the repository is added and configured, you can update your APT package lists and install Vault.
Command:
sudo apt update && sudo apt install vault
Step 4: Verify the Installation
After completing the installation, you can confirm that Vault has been set up properly by running a command to display its version.
Command:
vault --version
This should return the installed version of Vault, confirming that the installation was successful.
Vault is a powerful and reliable tool designed to safeguard sensitive information and manage secrets at an enterprise level. Whether you're storing API keys or dynamically generating credentials, Vault can streamline and secure your infrastructure.
To read more about How to Set Up HashiCorp Vault on Ubuntu, refer to our blog How to Set Up HashiCorp Vault on Ubuntu.